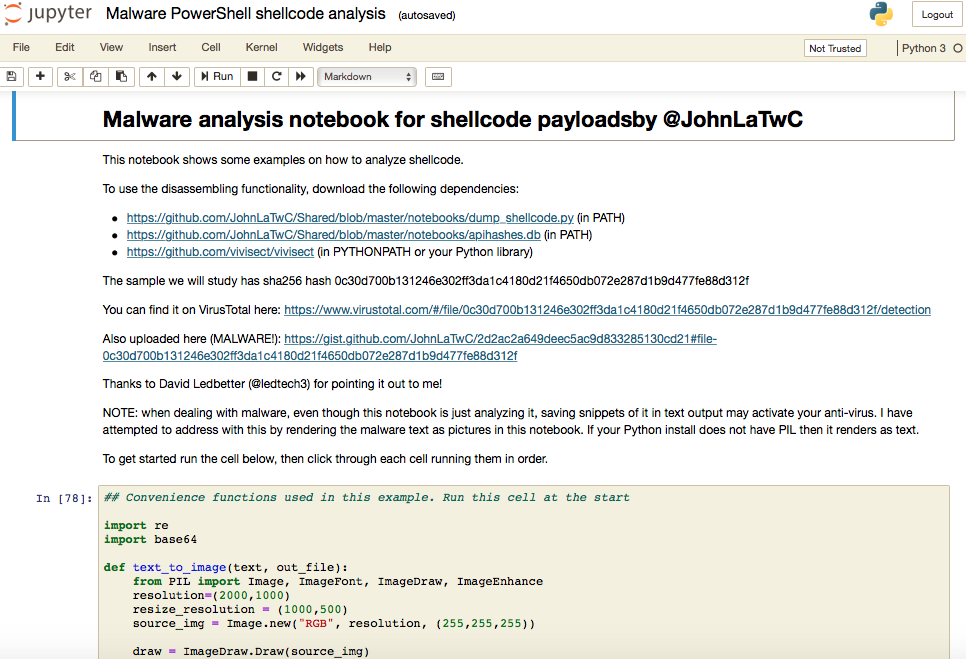
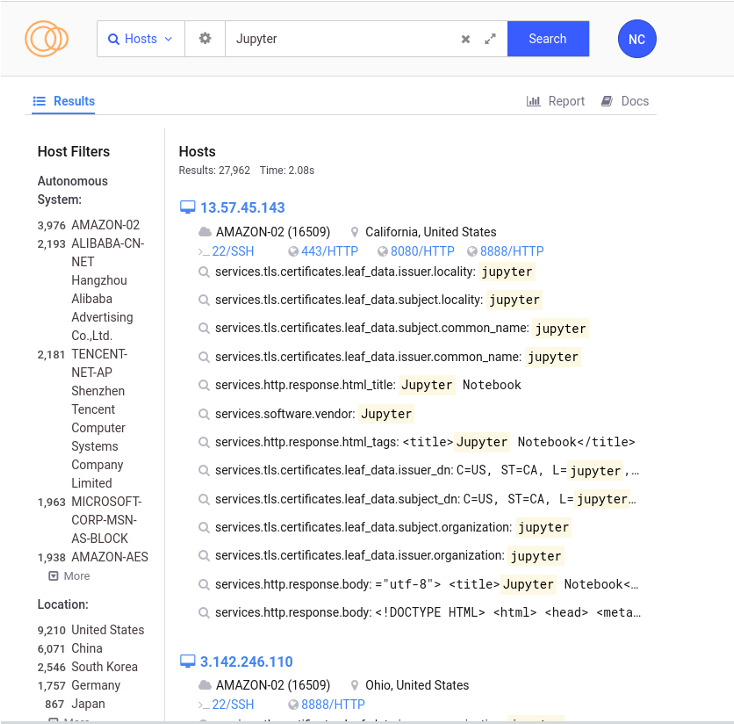
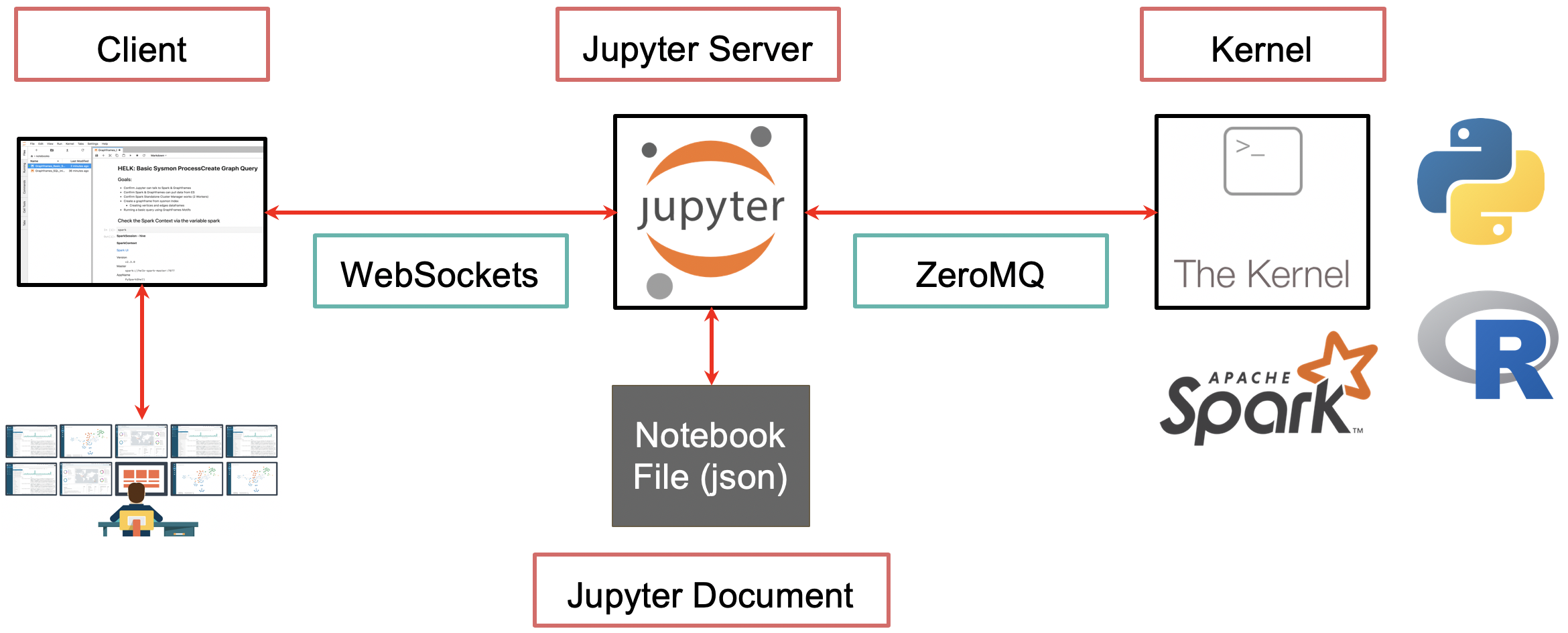
Qubitstrike - An Emerging Malware Campaign Targeting Jupyter Notebooks - Cado Security | Cloud Forensics & Incident Response
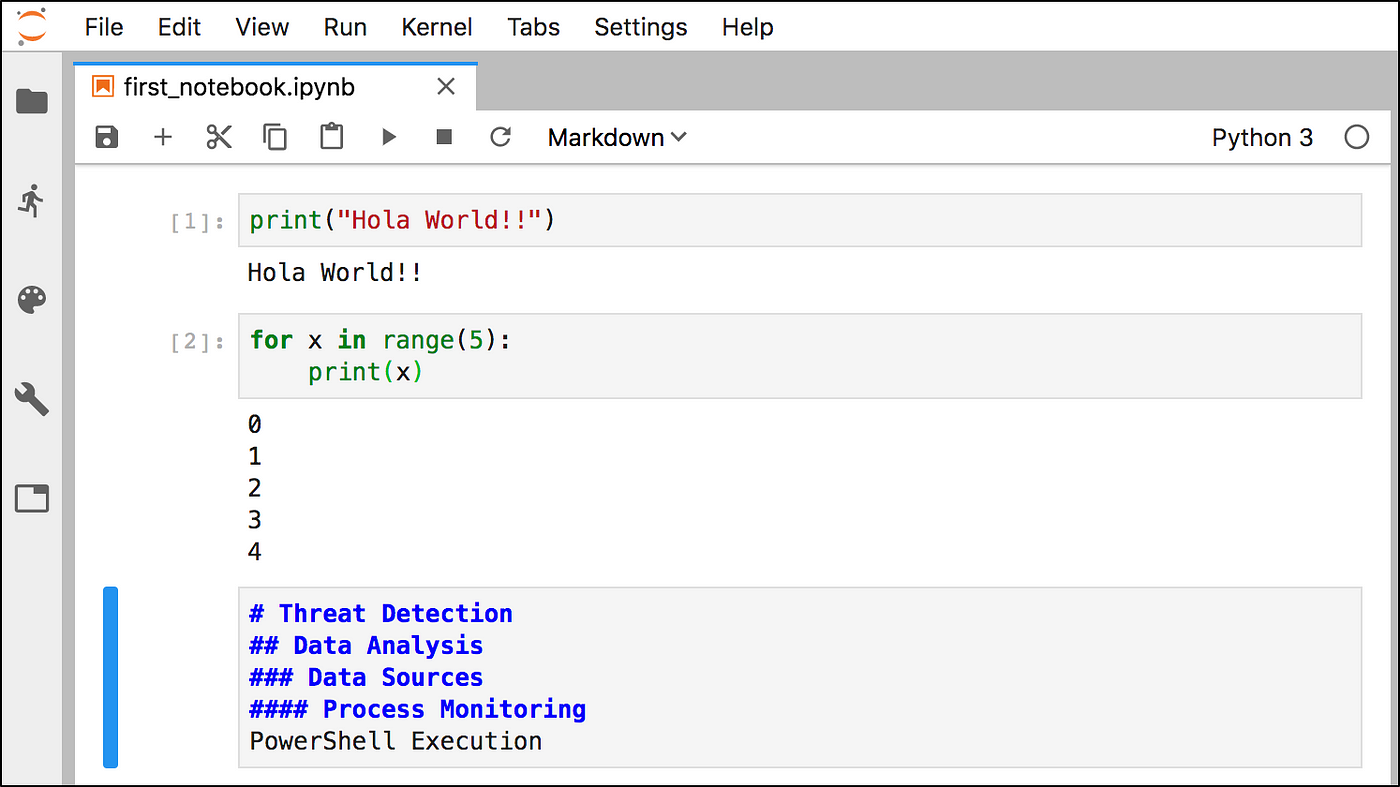
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members

Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members

amazon web services - Cannot obtain a trusted connection when hosting Jupyter Notebook on AWS EC2 instance - Stack Overflow
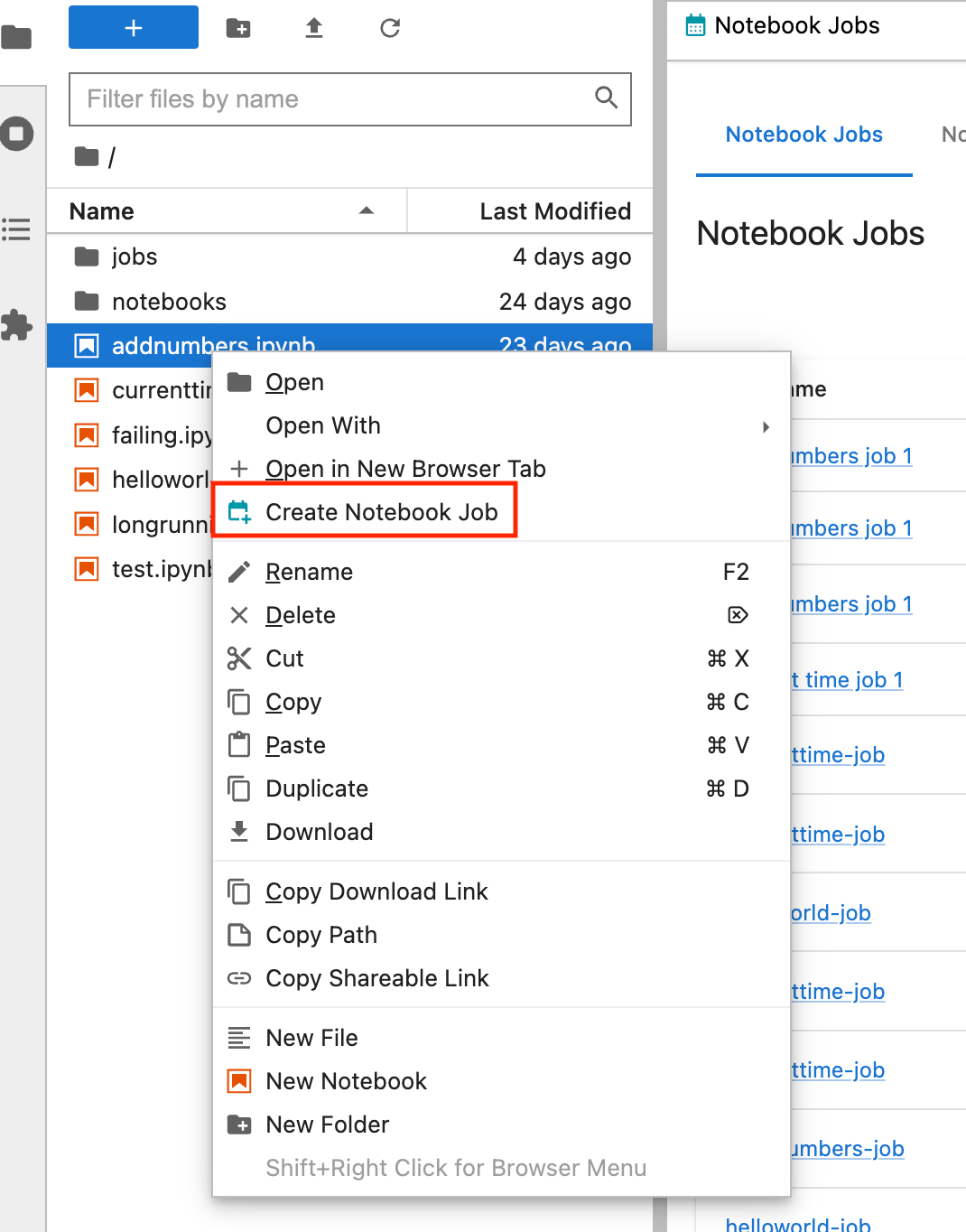
Introducing Jupyter Scheduler. The Open Source Jupyter team at AWS is… | by Jason Weill | Jupyter Blog